
Self-funded investigation into microSD cards finds 51 failed under load, while many performance and capacity claims proved to be fake
MicroSD card survey tested 200 models to uncover fakes, performance gaps, and endurance failures Fake…











For too long, security teams have had to wrestle with custom query languages just to ask basic questions of their SIEM. During the critical moments of an incident – when every second matters – analysts shouldn’t be slowed down by remembering syntax or troubleshooting formatting errors. They need to focus on outcomes: finding threats, scoping…

When we talk about cybersecurity, much of the focus tends to center around keeping attackers out—blocking unauthorized access, hardening perimeter defenses, and protecting login credentials. These are all important protections, but what happens once someone is inside the system, even with legitimate access? This is why we need defense-in-depth. Defense-in-depth is a cybersecurity strategy about…

Audrey forgets her indoor troubles when she’s outside in her garden. Source link

Audits are rarely simple. Security and compliance teams often find themselves buried in repetitive, time-consuming tasks—collecting logs from multiple systems, exporting reports from various tools, and manually reconciling data in spreadsheets. Evidence must be traced back to the correct controls, mapped against multiple frameworks, and cross-checked across departments. Requests from auditors add pressure, forcing teams…

Every October, Cybersecurity Awareness Month serves as a global reminder of just how quickly the digital world changes and how important it is to keep pace with it. This year’s theme, “Secure Our World,” feels especially urgent in the age of AI-powered threats.. For security and IT professionals, the question isn’t whether these shifts will…

Microsoft is addressing 176 vulnerabilities today, which seems like a lot, and it is. Curiously, Microsoft’s own Security Update Guide (SUG) for September 2025 Patch Tuesday only lists 86 vulns, and that’s because the SUG doesn’t include a large number of open source software (OSS) fixes published today as part of updates for Azure Linux/CBL-Mariner….

Thirty years ago, a peace-loving Austrian theologian spoke to Peter Thiel about the apocalyptic theories of Nazi jurist Carl Schmitt. They’ve been a roadmap for the billionaire ever since. Source link

Published September 30, 2025 Louis Vuitton, the luxury travel marque par excellence, staged the first major influential show of this Paris Fashion Week on Tuesday, wowing with a refined collection presented inside a royal apartment within the Louvre. Louis Vuitton – Spring-Summer 2026 – Paris Fashion Week – France – Paris – FashionNetwork.com And not…

New LightHouse Studio RCE module This week we’ve added a new module that exploits an unauthenticated template injection vulnerability (CVE-2025-34300) in Sawtooth Software’s Lighthouse Studio, allowing arbitrary Perl execution via survey templates in versions prior to 9.16.14. This module has the ability to exploit surveys which are hosted on either Linux or Windows servers. Thanks…
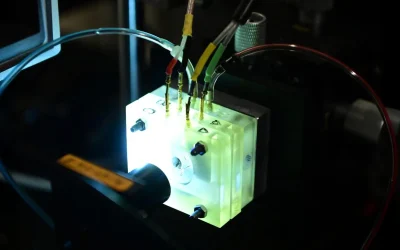
Shortly before his death in August 2025, A. James Hudspeth and his team in the Laboratory of Sensory Neuroscience at The Rockefeller University achieved a groundbreaking technological advancement: the ability to keep a tiny sliver of the cochlea alive and functional outside of the body for the first time. Their new device allowed them to…